Admin Security: Difference between revisions
No edit summary |
No edit summary |
||
| Line 48: | Line 48: | ||
'''Allow SIP connections from only Allowed IP''' permits to lock down the server to only authorized IP | '''Allow SIP connections from only Allowed IP''' permits to lock down the server to only authorized IP | ||
[[file:blockedip.png|400px]] | |||
'''Block known SIP scanners''' activate a special filter to stop any connection from known SIP scanners trying to identify your server as a potential target | '''Block known SIP scanners''' activate a special filter to stop any connection from known SIP scanners trying to identify your server as a potential target | ||
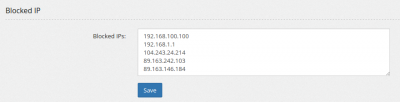
'''Blocked IPs''' contains the list of IP addresses or classes (like 192.168.0.0/16) always blocked from connecting to the server IP address | '''Blocked IPs''' contains the list of IP addresses or classes (like 192.168.0.0/16) always blocked from connecting to the server IP address | ||
| Line 64: | Line 64: | ||
If next to zero, the IP is going to be blocked. | If next to zero, the IP is going to be blocked. | ||
If you want, you can provide your own firewall script. All firewall scripts are in clear in /var/lib/asterisk/agi-bin/ | |||
The main check is done using /var/lib/asterisk/agi-bin/checkgeoipf2b.php and various scripts are run based on the options selected. | |||
Main script is /var/lib/asterisk/agi-bin/applyGeoIPfirewall.sh and it can be completely replaced providing a /var/lib/asterisk/agi-bin/applyGeoIPfirewall-custom.sh or you can add your own rules to /var/lib/asterisk/agi-bin/applyGeoIPfirewall-addition.sh | |||
== Raw traffic == | == Raw traffic == | ||
Latest revision as of 15:56, 28 February 2017
Taking care of your server security is really important. Every day there will be people around the globe trying to hack in your system and stole thousand of dollars worth of traffic.
You have several instruments to try to avoid being hacked and to minimize the damage from a successful hacking.
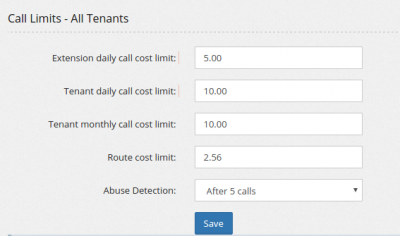
Call Limits
Call limits is the last protection against a successful hacking episode. You can limit how much you are ready to pay if the credentials for an extension or an entire tenant are compromised.
Extension daily call cost limit allows you to set a maximal amount of money an extension can use in a single day (from 00:00 to 23:59). If this amount is reached, the extension cannot dialout and a message is shown beside his call history entry. If an extension is compromised, then hackers should be able to use only up to this amount of money. Take in mind it seems to be available in the wild a method to fool asterisk making it to believe a call has been hang up while instead it is still continuining to run on your provider, leaving this option completely useless. Tenant daily call cost limit is the same as above, but extended to all extensions for the provider. Tenant monthly call cost limit is the same as above, but over one month period. Route cost limit is the maximum cost/minute allowed for a route destination. If a route destination has an higher cost, dialing it will be forbidden. Abuse Detection enables a monitoring of international calls. If more than X calls to the same international number are placed in 300 seconds (5 minutes), the extension is blocked
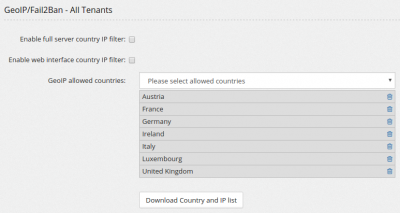
GeoIP/Fail2Ban
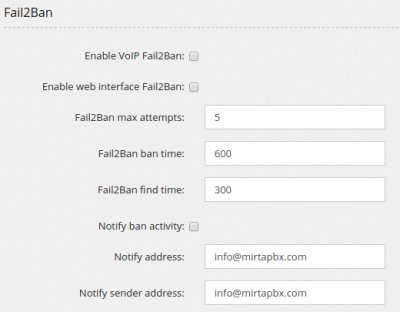
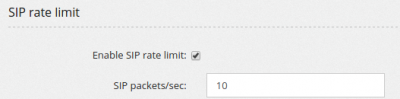
This is your first line of defense. GeoIP allows you to restrict access to your server from only some countries. Fail2Ban will monitor your system log files and if repeated attempts are detected, the offending IP will be banned. SIP rate limit allows you to define the maximal number of SIP messages your server can handle from the same IP address. Always allowed IP list allows you to define a list of IP that are always allowed to connect to your server. Blocked IP list allows you to define a list of IP that cannot connect to your server.
Enable full server country IP filter enables complete lock of external access to the server except from the countries listed. It includes SIP, web interface and SSH access. Enable web interface country IP filter enables lock of access to web interface except from the countries listed. User will be still allowed to access to the web login interface, but a message "You are not allowed to connect" will be shown upon access request. GeoIP allowed countries is the list of the countries allowed. It is important to periodically refresh the country list and to run at least once on all servers. This feature needs the geoip module loaded.
Enable VoIP Fail2Ban enables Fail2ban for SIP access Enable web interface Fail2Ban enables Fail2ban for Web access Fail2Ban max attempts sets the maximal number of attempts before being banned Fail2Ban ban time sets how long the IP will be banned Fail2Ban find time defines the interval in which the number of attempts are searched Notify ban activity defines if to notify every time an IP is banned (it can be really annoying) Notify address sets the address where to send the notice Notify sender address sets the sender address for the above notice
Enable SIP rate limit enables a kernel iptables module tracking the number of packets received by each single IP address, so no more than the defined amount of packets will reach your asterisk, protecting it by DOS attacks. SIP packets/sec is the number of packets per seconds allowed.
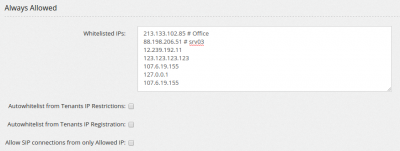
Whitelisted IPs contains the list of IP addresses or classes (like 192.168.0.0/16) always allowed to connect to the server IP address Autowhitelist from Tenants IP Restrictions automatically whitelist IP defined as restriction in tenant configuration Autowhitelist from Tenants IP Registration is probably mandatory if you think to run Fail2ban. It whitelists every IP from which a phone successful registers. In this way you can avoid having an entire client being blocked when a single phone in their local network has a bad password Allow SIP connections from only Allowed IP permits to lock down the server to only authorized IP
Block known SIP scanners activate a special filter to stop any connection from known SIP scanners trying to identify your server as a potential target Blocked IPs contains the list of IP addresses or classes (like 192.168.0.0/16) always blocked from connecting to the server IP address
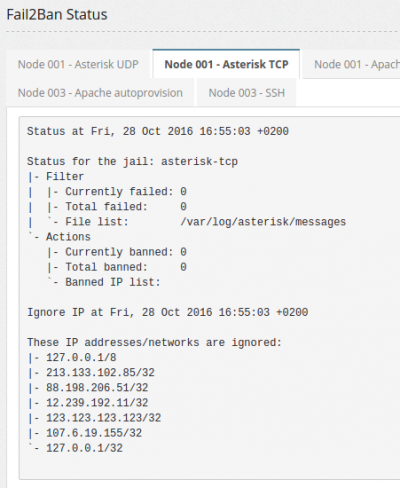
This section shows the status of Fail2ban on every node in the cluster
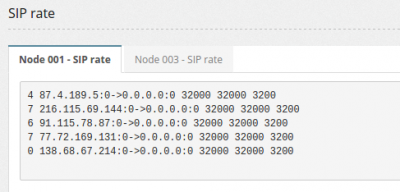
This section shows the list of IP seens in the latest seconds with the cumulative counter about the IP packets received. The important is the number highlighted in the following example:
4 87.4.189.5:0->0.0.0.0:0 32000 32000 3200
If next to zero, the IP is going to be blocked.
If you want, you can provide your own firewall script. All firewall scripts are in clear in /var/lib/asterisk/agi-bin/
The main check is done using /var/lib/asterisk/agi-bin/checkgeoipf2b.php and various scripts are run based on the options selected.
Main script is /var/lib/asterisk/agi-bin/applyGeoIPfirewall.sh and it can be completely replaced providing a /var/lib/asterisk/agi-bin/applyGeoIPfirewall-custom.sh or you can add your own rules to /var/lib/asterisk/agi-bin/applyGeoIPfirewall-addition.sh
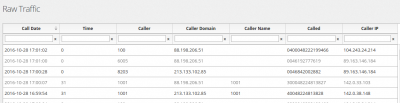
Raw traffic
You can have a look to the SIP traffic received by the server, so you can easily locate offenders or debug call issues, like when a provider is sending calls from a different IP address than configured. You can easily get the PCAP of the packet received or block it by adding to the list of Blocked IP addresses. Please note a blocked IP address will continue to be received by voipmonitor used to provide the raw traffic.