AAstra/Mitel 6869i: Difference between revisions
(Created page with "Provisioning this model is a bit trickier than usual. At boot time the phone requires several files in order # security.tuz # startup.cfg # aastra.cfg If aastra.cfg file is...") |
No edit summary |
||
| Line 7: | Line 7: | ||
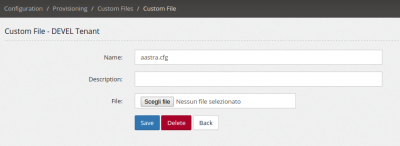
If aastra.cfg file is not obtained from the provisioning server, no other files are requested. As you can see, no file containing the MAC address is yet requested. To make it go further is needed to create an empty file and upload in the custom file section. | If aastra.cfg file is not obtained from the provisioning server, no other files are requested. As you can see, no file containing the MAC address is yet requested. To make it go further is needed to create an empty file and upload in the custom file section. | ||
[[aastra__empty_file.png|400px]] | [[file:aastra__empty_file.png|400px]] | ||
Once this file is offered to the phone using the provisioning server, the phone requires two additional files: | Once this file is offered to the phone using the provisioning server, the phone requires two additional files: | ||
| Line 24: | Line 24: | ||
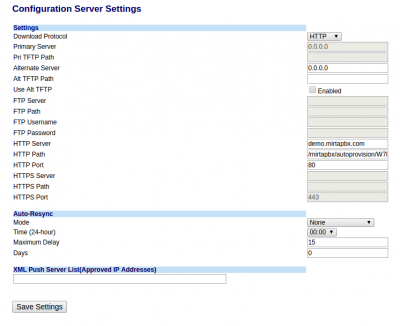
In the phone choose the preferred method between HTTP and HTTPS and provide the server hostname, without the protocol part, in my case just demo.mirtapbx.com and the path for the provisioning, like /mirtapbx/autoprovision/W7H85Znu7nDrnPn6/ | In the phone choose the preferred method between HTTP and HTTPS and provide the server hostname, without the protocol part, in my case just demo.mirtapbx.com and the path for the provisioning, like /mirtapbx/autoprovision/W7H85Znu7nDrnPn6/ | ||
[[aastra6869iprovisioning.png|400px]] | [[file:aastra6869iprovisioning.png|400px]] | ||
Please note on the model I have, it was not possibile to use HTTPS because the certificate was crashing the phone, maybe for a too long certificate chain. A better (more expensive) certificate, with a shorter chain, may work. | Please note on the model I have, it was not possibile to use HTTPS because the certificate was crashing the phone, maybe for a too long certificate chain. A better (more expensive) certificate, with a shorter chain, may work. | ||
Latest revision as of 07:59, 30 October 2016
Provisioning this model is a bit trickier than usual. At boot time the phone requires several files in order
- security.tuz
- startup.cfg
- aastra.cfg
If aastra.cfg file is not obtained from the provisioning server, no other files are requested. As you can see, no file containing the MAC address is yet requested. To make it go further is needed to create an empty file and upload in the custom file section.
Once this file is offered to the phone using the provisioning server, the phone requires two additional files:
- 6869i.cfg
- {MAC}.cfg
With {MAC} replaced with the MAC address of the phone.
For documentation completeness, some files are requested too:
- aastra.lic
- {MAC}.lic
- 6869i.st
In the phone choose the preferred method between HTTP and HTTPS and provide the server hostname, without the protocol part, in my case just demo.mirtapbx.com and the path for the provisioning, like /mirtapbx/autoprovision/W7H85Znu7nDrnPn6/
Please note on the model I have, it was not possibile to use HTTPS because the certificate was crashing the phone, maybe for a too long certificate chain. A better (more expensive) certificate, with a shorter chain, may work.